We’ve only touched on the NSA spy stories a few times lately; but this one is dedicated to the good folks at NSA contractor Lockheed Martin.
Ever since I wrote “The NSA, CIA Venture Capital, and Peter Thiel”, Lockheed Martin has logged on to my Statcounter every stinkin’ day. They are like a dog turd I can’t quite scrape off my boot, so I guess I’d better just get used to it.
And people wonder why I don’t use Facebook…
First of all, this whole kerfluffle about NSA spying is nothing new. The type of system used began in the cold war 1960’s and became known as the “Echelon” program. You can read about the background of Echelon on this Wikipedia page.
The revelations of former contract employee Edward Snowden are not so new, except for the fact that we now know that most, if not nearly all information is being collected and processed by private contractors like Snowden’s former employer Booze Hamilton Allen, the folks at Lockheed Martin, and other firms.
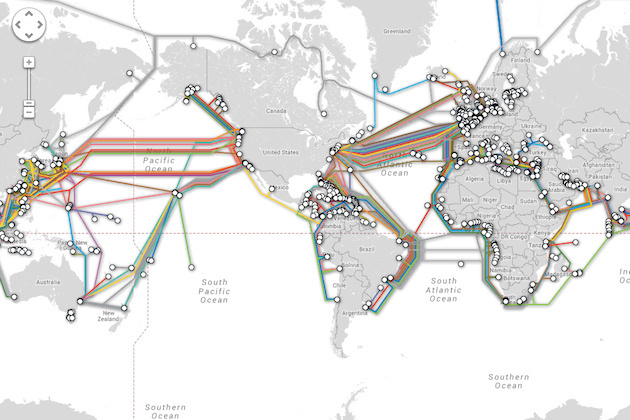
But there is more to the big picture. Here’s a map of undersea (submarine) communication cables:
A couple of times every year we read about some submarine cable breaking for some unexplained reason. Well, now we know that in some cases those cables are being tapped.
The website “motherboard.vice.com” has an article describing the process:
Wiretapping Undersea Fiber Optics Is Easy: It’s Just a Matter of Money
(excerpt)
“I think the notion of efficiency might be a misnomer or mischaracterization when talking about tapping undersea cables,” he said in a phone interview. “Let’s say you want to tap the trans-Atlantic, trans-Pacific cables and all other pathways—and you want to tap all of them—the number of cables is pretty small. It’s a four-digit number or less.” In other words, there aren’t many undersea cables on the planet, and their locations are mapped. In March of this year the Egyption navy caught three divers attempting to sever the submarine cable SEA-ME-WE 4, which runs from France to Singapore, and connects Egypt to the internet. These were men in a dinghy. Think of what well-budgeted government agencies can do.
*
Cable landing stations, not undersea regeneration points, are the likely locations for tapping, according to Kapela. “That’s the obvious place to intercept, or near that place—upstream of it.” Here, user data can be electronically copied in a way that is completely invisible. “There are a lot of possibilities there, so many such that you’d have to argue with special pleading to say that it is not practical,” said Kapela, adding that one should assume it is going to happen. Lovely news.”
Over at the website “Antifascist Calling” they ran this doosey of a story:
Documents Show Undersea Cable Firms Provide Surveillance Access to US Secret State
(excerpt)
“Documents published last week by the Australian web site Crikey revealed that the US government “compelled Telstra and Hong Kong-based PCCW to give it access to their undersea cables for spying on communications traffic entering and leaving the US.”
The significance of the disclosure is obvious; today, more than 99 percent of the world’s internet and telephone traffic is now carried by undersea fiber optic cables. An interactive submarine cable map published by the Global Bandwidth Research Service is illustrative in this regard.
Since the late 1960s as part of its ECHELON spy project, the United States has been tapping undersea cables to extract communications and signals intelligence. In fact, projects such as Operation Ivy Bells, a joint Navy-NSA secret intelligence program directed against the former Soviet Union was designed to do just that.
Prefiguring the Bush administration’s warrantless wiretapping scandal which broke in 2005, the Associated Press reported that a $3.2 billion Navy Seawolf class submarine, a 453-foot behemoth called the USS Jimmy Carter, “has a special capability: it is able to tap undersea cables and eavesdrop on the communications passing through them.”
———–
It’s a lengthy and well researched article, available at the embedded link.
But there’s something even more sinister going on; Remember the death of Journalist Michael Hastings a few weeks back? Hastings, whose Rolling Stone article brought down General Stanley McChrystal was killed in a freakish car wreck. He had contacted friends and said he was on to something big, and that the FBI was watching him.
Well, “The economicpolicyjournal.com” has a mind-blowing report that ties Hastings and hacker Barrett Brown:
“Hastings has been linked to Barrett Brown, who the government alleges is the leader of the hacker group Anonymous. Brown is in jail and is being held without bail. The web site Free Barrett Brown reports:
Having previously been raided by the FBI on March 6, 2012 and not charged with any crime in relation to that incident, on September 12, 2012 Barrett Brown was again raided and this time arrested by the Federal Bureau of Investigation while he was online participating in a Tinychat session. He was subsequently denied bail and detained without charge and adequate medical treatment for over two weeks while in the custody of US Marshals. In the first week of October 2012, he was finally indicted on three counts.
These charges are related to alleged activities or postings on popular websites such as Twitter and YouTube, in which he postured for the return of property which was taken from him in March, and expressed frustration at the targeted campaign against him and a member of his family. The Department of Justice issued a press release at the time.
On December 4, 2012 Barrett was indicted by a federal grand jury on twelve additional counts (see: DOJ press release) related to data from the Stratfor breach.
Also, according to the web site, Hastings was planning to interview Brown:
Before his untimely death, Hastings was working on a story about Barrett, announcing mysteriously to his followers “Get ready for your mind to be blown.” Hastings had been in touch with Barrett’s lawyers, and intended to interview him in June for the story. Barrett has been in prison for 281 days pending trial, and faces over a hundred years imprisonment for what Hastings called ”trumped up FBI charges regarding his legitimate reportorial inquiry into the political collective known sometimes as Anonymous.”
Before his suspicious death in a fiery car crash, Hastings seemed to confirm this planned interview, in a tweet and hinted it was relative to a very big story:
@ronbryn @BarrettBrownLOL working on it. there was an election, and still a few wars going on. but get ready for your mind to be blown.
— Michael Hastings (@mmhastings) January 24, 2013
Barrett, at the time he was arrested,was studying Endgame. The Nation reports:
Brown began looking into Endgame Systems, an information security firm that seemed particularly concerned about staying in the shadows. “Please let HBGary know we don’t ever want to see our name in a press release,” one leaked e-mail read. One of its products, available for a $2.5 million annual subscription, gave customers access to “zero-day exploits”—security vulnerabilities unknown to software companies—for computer systems all over the world. Business Week published a story on Endgame in 2011, reporting that “Endgame executives will bring up maps of airports, parliament buildings, and corporate offices. The executives then create a list of the computers running inside the facilities, including what software the computers run, and a menu of attacks that could work against those particular systems.” For Brown, this raised the question of whether Endgame was selling these exploits to foreign actors and whether they would be used against computer systems in the United States. Shortly thereafter, the hammer came down.
The FBI acquired a warrant for Brown’s laptop, gaining the authority to seize any information related to HBGary, Endgame Systems, Anonymous and, most ominously, “email, email contacts, ‘chat’, instant messaging logs, photographs, and correspondence.” In other words, the FBI wanted his sources.
So what is Endgame? According to Darker Net:
Endgame [is] a company that specialises in hacking on behalf of NSA. Endgame also offers its intelligence clients — e.g. Cyber Command, NSA, CIA and MI6, etc — a unique map, called Bonesaw, showing exactly where targets are located.
*
“The “services” offered by Endgame include offensive and defensive vulnerability research including software called Bonesaw supporting the detection and mitigation of cyber threats. This basically means that they cover both offensive and defensive aspects of computer security. What they can do is show what computers exist at specific locations and show the user of “Bonesaw” what software vulnerabilities are on those computers, making attacks easy against citizen, business or government systems across the planet.(18) Bonesaw has information in it about both threats and targets and can connect the two, for the low, low price of $2.5million per customer per 25 exploits according to Emails found by Anonymous in 2011.”
—————————————
Now here’s what we need to think about; how much of this data is being sold on the private market?
And who is being blackmailed with sensitive information? Our Congress?
Well here’s a shocker that has been going around, this article from The Huffington Post explains a lot:
Russ Tice, Bush-Era Whistleblower, Claims NSA Ordered Wiretap Of Barack Obama In 2004
(excerpt)
“Russ Tice, a former intelligence analyst who in 2005 blew the whistle on what he alleged was massive unconstitutional domestic spying across multiple agencies, claimed Wednesday that the NSA had ordered wiretaps on phones connected to then-Senate candidate Barack Obama in 2004.
Speaking on “The Boiling Frogs Show,” Tice claimed the intelligence community had ordered surveillance on a wide range of groups and individuals, including high-ranking military officials, lawmakers and diplomats.
The drug https://levitralab.com begins to act approximately two hours after ingestion. In the description of the tablets indicated that the drug acts about 10 hours. My husband’s effect lasted for two days.
“Here’s the big one … this was in summer of 2004, one of the papers that I held in my hand was to wiretap a bunch of numbers associated with a 40-something-year-old wannabe senator for Illinois,” he said. “You wouldn’t happen to know where that guy lives right now would you? It’s a big white house in Washington, D.C. That’s who they went after, and that’s the president of the United States now.”
Host Sibel Edmonds and Tice both raised concerns that such alleged monitoring of subjects, unbeknownst to them, could provide the intelligence agencies with huge power to blackmail their targets.”
——————————————
Simply out of control…



It’s quite possible that our politicians aren’t the ones in charge of the country anymore. It’s the people that are blackmailing them that the run the show.